“Jope” Virus
Jope is a DJVU family of ransomware-type infections1. This infection encrypts important personal files (video, photos, documents). The encrypted files can be tracked by specific “.jope” extension. So, you can’t open them at all.
In this tutorial, I will try to help you remove Jope virus without any payment. Also, I will assist you in decoding your encrypted files.
What is “Jope”?
Jope can be correctly identify as a ransomware infection.
Ransomware is a specific kind of virus that encrypts your documents and then forces you to pay for them. Note that DJVU (aka STOP) ransomware family was first revealed and analyzed by virus analyst Michael Gillespie2.Jope is similar to other representatives of the same family: Mado, Opqz, Npsk. It encrypts all popular file types. Hence, you cannot work with the your documents. Jope virus adds its own “.jope” extension into all files. For example, the file “video.avi”, will be amended into “video.avi.jope”. As soon as the encryption is accomplished, Jope drops a special text file “_readme.txt” and adds it into all folders that contain the modified files.
Here is a short details for the Jope ransomware:
| Ransomware family3 | DJVU/STOP4 ransomware |
| Extension | .jope |
| Ransomware note | _readme.txt |
| Ransom | From $490 to $980 (in Bitcoins) |
| Contact | helpdatarestore@firemail.cc, helpmanager@mail.ch |
| Detection | Ransom.Rapid, Win32/Agent.UBA, Ransom.FTPC |
| Symptoms | Most of your files (photos, videos, documents) have a .jope extension and you can’t open it |
| Fix Tool | See If Your System Has Been Affected by .jope file virus |
This text asking payment is for restore files via decryption key:
The cryptography algorithm used by Jope is AES-256. So, if your documents got encrypted with a specific decryption key, which is totally distinct and there are no other copies. The sad reality is that it is impossible to recover the information without the unique key available.
In case if Jope worked in online mode, it is impossible for you to gain access to the AES-256 key. It is stored on a remote server owned by the criminals who distribute the Jope ransomware.
For receiving decryption key the payment should be $980. To obtain the payment details, the victims are encouraged by the message to contact the frauds by email (helpdatarestore@firemail.cc).
UPD.06.04.2020. We got some users’ reports that they got a modified readme.txt file. Fraudsters now asking for much bigger sum for decrypting – up to 1500$, if you don’t do this in 72 hours, but also they menacing user to delete all his files. It’s the same tactic that a lot of another ransomware did.
UPD. 22.04.2020 We also got some reports about one more “price-list”. In some versions of Jope ransomware, victims are asked about 500$ for decryption, regardless of the moment they are making this payment.
UPD. 25.04.2020 Some users told us about another payment requirements. They were asked about a sum of 0.3 BTC, and the time-frame of avaliable “discount”, when the victim may pay 0.1 BTC was decreased to 48 hrs.
Do not pay for Jope!
Please, try to use the available backups, or Decrypter tool
_readme.txt file also indicates that the computer owners must get in touch with the Jope representatives during 72 hours starting from the moment of files where encrypted. On the condition of getting in touch within 72 hours, users will be granted a 50% rebate. Thus the ransom amount will be minimized down to $490). Yet, stay away from paying the ransom!
I certainly recommend that you do not contact these crooks and do not pay. The one of the most real working solution to recover the lost data – just using the available backups, or use Decrypter tool.
This advice is not just words. In spite of reasonless of this idea, you may also be forced to pay. We have enough reports of users, who tried to talk with fraudsters. One of the most popular answer of them – “pay us, or we will delete all your files”. And that’s no matter, did you pay or not, croocks will later sell a database of e-mails of their victims, who contacted them, with your e-mail inside. And, in positive case, you will just get an advetiserment spam on your mailbox.
Another mean action ransomware distributors usually do is distributing a malware pack with their own decryptor. They are ofering to use this program in readme.txt. So, users who paid for Jope ransomware decryption, or found an offline key are downloading this decryptor and surprising that their PC got an adware and browser hijacker, or sometimes someting worse, like trojan or even backdoor.
Yes, they can put on an act that they are fair-playing, and decrypt one or two your files (they’re calling it “decryption test”). But, nonetheless, you have literally no guarantee that they will decrypt your files after payment, even if they have decrypted some of your files before.
These weekends one of users who was been attacked by Jope ransomware reported about a hot message from croocks. This user contacted them to “test” their decryptor. Two days later, they send him a ranting, where they told about file encryption as a punishment for stolen software using. Not a good justification for fraudsters who also steals a lot of personal data and find such an idiotic names for new ransomware.
Important note : we have no approved facts about Jope ransomware to delete itself from victim’s PC after the encryption. So, you may check readme.txt files it dropped in every folder – that’s a big chance that in one of this files will contain an offline key. Using it you can decrypt all your files without any payment. Ransomware distributors have left a link to full manual of decrypting inside readme.txt.
There are also a lot users who told us about third persons, who claimed that they are able to deal with your ransomware by theirselves. You need to understand that no one can vouch for this figures, and no one can be sure about their motives. There were a lot of cases in the past when such “helpers” can be a ransomware distributor’s agent, who will force you to pay to ransomware creators indirectly. Some figures can even claim that they are able to decrypt some cases that are currently cannot be dectrypted with all known means.
You can also check if you have an offline key. Open PersonalID file, which is located in SystemID folder on C:/ disk. If this file contains any entity which ends on “t1” – you’re lucky, because if Jope ransomware has encrypted your files with an offline key, it’s much easier to decrypt them.
UPD 19.04.2020. We got an information from Emsisoft Decryptor developers about successfull collecting of big amount of offline keys to Jope ransomware. So, nowadays, the decryptor we are offering below can decrypt the majority of Jope cases. Thanks a lot to users who were helping Emsisoft team to find all this keys.
The peculiarity of all such viruses apply a similar set of actions for generating the unique decryption key to recover the ciphered data.
Thus, unless the ransomware is still under the stage of development or possesses some hard-to-track flaws, manually recovering the ciphered data is a thing you can’t perform. The only solution to prevent the loss of your valuable data is to regularly make backups of your crucial files.
Note that even if you do maintain such backups regularly, they ought to be put into a specific location without loitering, not being connected to your main workstation.
One of the most unpleasant cases is when Jope ransomware injects himself into your backup files. Seeing ransomware attack results – encrypted files with .jope extensions, _readme.txt files in every folder – users are acting without hesitation, using a backup to restore a system from the version without ransomware. Nonetheless, such users could have a malicious joke, when they finish their backup and discover that they’ve got a ransomware attack, again.
Also, be very careful while using OneDrive backups. It performs a backup-creating procedure without any notification, and re-writing the old backup in process of creating a new one. So, if you rely on OneDrive backups as on the backup source – turn it off if you got a ransomware or any malware, because your backup will be re-written with already encrypted files.
In spite of injection in backup files, Jope ransomware can also perform a very mean action with the backups, that was been created using basic Windows methods. Ransomware blocks an access to such backups, or even delete them, if user didn’t move them away of default directory and got a specific Jope ransomware edition. That’s why the best solution for backup creating is non-proprietary software, and holding them on separate storage device or cloud storage.
Jope ransomware can also perform some actions with your “hosts” file. Since ransomware always adds it’s entities to the registry and modifies some system files, it adds a Microsoft update server to hosts. That action blocks an access to this site, so your computer cannot get an update that can wipe out some parts of ransomware.
A common feature of all ransomware is that their start is delayed by default. After it’s an injection in your PC you won’t notice it at all. Jope ransomware will start encryption only after it gets fitting command from the command server, which is driven by ransomware distributors. And when user notices files with .jope extensions and readme.txt files – it’s already too late for any action, excluding usage of Decryption tool and Anti-malware software.
One more feature, that can differ from one ransomware to another, is it’s encryption behaviour. It can differ even between different editions of the same ransomware. Jope ransomware, for example, in majority of it’s editions have quite fast start – after the encryption process launched, it detects oftenly-used files, and encrypt them. Then, it focuses on USB-devices, and then starts to encrypt chaoticaly everything on your PC.
We also detected a several cases when Jope ransomware re-encrypted already encrypted file. That was usually happening when the user had some files undecrypted after previous ransomware attack, and then got Jope on his PC. To decrypt such files, you need to do the decryption twice.
Accroding to data we got from users whose files was been encrypted, Jope ransomware sometimes encrypt only one disk – C:/ or D:/, depending on where was ransomware files located. So, an old advice said that “do not download and install anything on C:/ disk” in case of Jope ransomware is not actual – if you have no important data on C:/ disk, you can ignore ransomware attack for some time. But, again, that is true only if Jope ransomware edition you got is not able to encrypt another disks, in spite of one he was located on.
We checked a lot of data about different ransomware from STOP/Djvu family, and draw a conclusion that such behaviour is typical for the whole family, not only for Jope ransomware. They always randomly encrypts one or both disks, and can the same optionally encrypt your USB flash drives
If you plugged in a USB flash drive, or external HDD, during the encryption process – your files may be encrypted, too. But there were also some cases when Jope ransomware copied it’s .exe file to external drive, in spite of common encryption like it did on the PC. Thus, user’s USB flash drive became a portable ransomware carrier. To remove such a threat you need to have an anti-malware software that is able to perform with external disks.
Like a lot of other ransomware, Jope ransomware having troubles with lagre files encrypting. Trying to encrypt large files (>1GB), it can just got an error and only add it’s .jope extension without real encryption. So, you can try to get an access to your lagre files. Just delete .jope extension from the file name and try to open them in usual way.
One more chance to reach your files is the bug with archieves encryption. If an archieve contains several files and has a relatively big common size, Jope ransomware can just miss some files or just rename them in spite of encryption (like it does with large files).
Another feature of all STOP/Djvu ransomware family is that ransomware encrypts only first 150 kilobytes of the file. So, MP3, AVI, MP4 or other files that have relatively big size can be run even after encrypting. For example, Winamp is able to open this files, but with unavoidable “silence” during the first seconds of recording. That happens because this part of the file is encrypted. This bug/feature can be useful, if you want to listen to music or to watch a video, but your files was been encrypted by Jope ransomware.
One important detail about decryption . JPEG/JPG images have a format oddity that causes file pairs to be specific to each source of pictures, rather than the file format in general. As an example, if you have shots from two different cameras, and submit a file pair from the group of pictures from one of the cameras, then the decrypter will only be able to decrypt files from the camera that the file pair came from. In order to decrypt all JPEG/JPG images, you will need to submit file pairs from every source you’ve obtained those pictures from.
Also, for obvious reasons, Jope ransomware has a quite complex mechanism, that prevents user’s attempts to avoid encryption. Ransomware adds himself into RunOnce registry key, which allows him to launch with Windows launch, so user cannot stop encryption process without using skillful tricks like starting the system with command line, or so, that is disabling any software launch excluding proprietary Windows software.
Some modifications of Jope ransomware can also add it’s readme.txt file in RunOnce registry key, so every time user starts his PC – he will se an annoying reminder about payment. Also, if ransomware activity wasn’t been spotted before PC shutdown – such “surprise” can be used as a first notification about encrypted files, which can turn the victim in panic, and, sometimes, force him or her to pay.
Another feature of Jope ransomware is computer slowdown. Of course, that’s actual if you have a weak PC, but it can be also crucial for quite powerful machines, that are working in hard-load mode, executing rendering, 3D modelling or any other heavy-consuming processes. So, if you noticed any inhibition of your PC perfomance, lagspikes or so – it’s a serious reason to do a full-scan of your machine.
There are very rare cases when Jope ransomware was able to delete any files or software from the victim’s PC. Reportedly, the ransomware started a process named “send” in the task manager, which was not able to be closed. Then, the encrypted files with .jope extension appeared and, simultaneously, a lot of software was been deleted. Such behaviour is very strange for ransomware, so we think it can be a joint action of Jope ransomware and another malware.
For instance, the backup may be kept on the USB flash drive or some alternative external hard drive storage. Optionally, you may refer to the help of online (cloud) information storage.
Needless to mention, when you maintain your backup data on your common device, it may be similarly ciphered as well as other data.
For this reason, locating the backup on your main PC is surely not a good idea.
How I was infected?
Jope has a various methods to built into your system. But it doesn’t really matter what concrete way had place in your case.
Crackithub[.]com, kmspico10[.]com, crackhomes[.]com, piratepc[.]net — sites that distribute JOPE Ransomware. Any app downloaded from there sites can be infected your PC by this virus.
Another such sites:
xxxxs://crackithub[.]com/adobe-acrobat-pro/ xxxxs://crackithub[.]com/easyworship-7-crack/ xxxxs://kmspico10[.]com/ xxxxs://kmspico10[.]com/office-2019-activator-kmspico/ xxxxs://piratepc[.]net/category/activators/ xxxxs://piratepc[.]net/startisback-full-cracked/
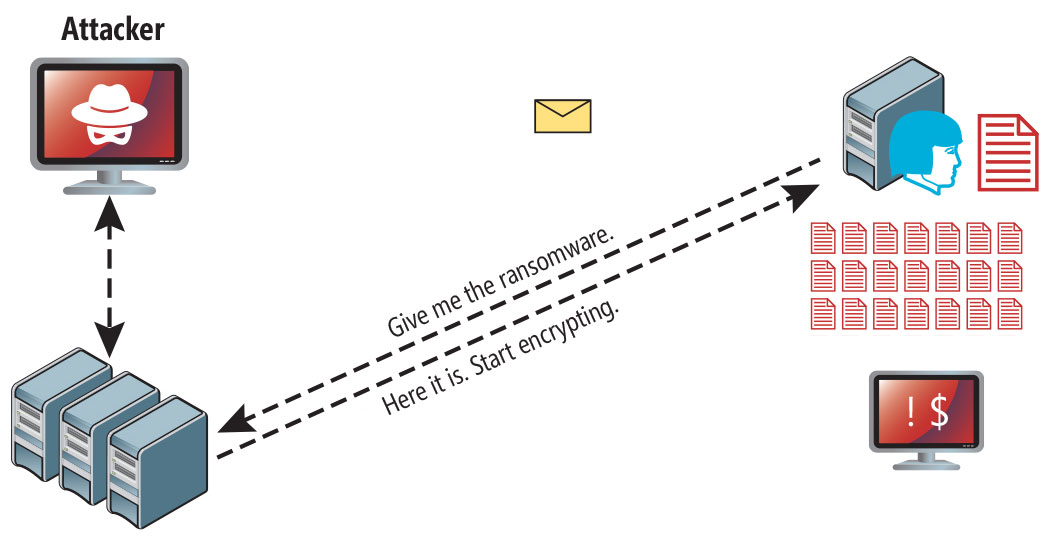
Jope ransomware attack following a successful phishing attempt.
- hidden installation along with other apps, especially the utilities that work as freeware or shareware;
- dubious link in spam e-mails leading to the Jope installer
- online free hosting resources;
- using illegal peer-to-peer (P2P) resources for downloading pirated software.
There were cases when the Jope virus was disguised as some legitimate tool, for example, in the messages demanding to initiate some unwanted software or browser updates. This is typically the way how some online frauds aim to force you into installing the Jope ransomware manually, by actually making you directly participate in this process.
Surely, the bogus update alert will not indicate that you are going to actually inject the Jope ransomware. This installation will be concealed under some alert mentioning that allegedly you should update Adobe Flash Player or some other dubious program whatsoever.
Of course, the cracked apps represent the damage too. Using P2P is both illegal and may result in the injection of serious malware, including the Jope ransomware.
For a long time, a big part (about 26%) of all Jope ransomware injection was attributed to cracked software and games. Majority of users who got a ransomware in such way told us that they were using torrent-trackers to search and download the software they need. That’s not a big surprise that torrent-trackers are not the safest software source, especially if paid program was been cracked and then distributed in such way. But last time such cases can be spectated much more often and massive.
Another popular way of Jope ransomware injection is “Update your browser!” advetiserments, that are offering you to get the last version of Chrome, Firefox, Opera or any other browser you are using, even if it is already up to date. After following this ad, user gets a file that contains ransomware, and in some time it starts encrypting process.
We also need to mention that the possibility of successfull decryption using any decryption tool, as well as any other data recovery, depends on the changes that was been made from the moment of encryption finish to decryption start. So, the more you use your PC, the more you are modifing your files – the less chances of decryption 100% of your files you have.
Jope ransomware, like majority of other ransomware, gets your computer in bundle with another malware. Usually, you get some kind of browser hijacker or backdoor. In case of something lite, like hijacker, user can remove it even manually, but backdoor or any other “sneaky” malware will hide inside of your PC, but you can still detect it in many ways in spite of anti-malware software. But anyway, if you get a lite malware – that’s a reason to start a full scan in your antivirus, because it can be a sign of something much more serious.
According to a big number of reports, one of the most popular malware, that is distributed together with Jope ransomware, is a browser hijacker-adware. It changes your search engine to Yandex and every half hour opens a separate window of your browser, full of disgusting ads. So, if you are suffering of hijacker/adware with such symtoms, I’d recommend you to start a full scan of your PC as soon as possible.
Last time there are also several reports about Vitosc.xyz redirector appearance before Jope ransomware attack. Vitosc.xyz redirects your address bar searches to the site of the same name – vitosc.xyz, which contains different advetiserments.
Analysing the last statistic, I can conclude that a lot of Jope ransomware was been distributed as a part of an old software versions for specific needs. An example of such software is Photoshop 7.0, 5.5; AutoCAD 15-18, IMGburn, MagicISO and so on. An old versions of this program can be used due to weak PC configuration, or because of GUI changes that was been implemented in new versions of this software. An installer offers you to disable some PUPs that are usually distributed with freeware software, but no one was been offered to disable Jope ransomware installation. As a result, Jope starts encrypting instantly after installation.
Several users told us about an unusual ransomware downloading method. In stead of ransomware, they at first got potentially unwanted program of some sort, but later this PUP started a downloading in the background. A strange file named 421E.tmp.exe appeared, then their file were encrypted by Jope ransomware.
UPD 12.04.2020. Our team got a lot of reports about a massive spamming of potential victims with dubious e-mails. Such messages usually contain a request for payment of the invoice, that is attached below. So, to look at this invoice, you need to download it and open the file. But instead of invoice, you will likely see a very low quality scan of check of some sort, and a Jope ransomware, that starts encryption immediately after your have openen the downloaded file.
UPD.14.04.2020. Ransomware distributors decided to use another way of Jope ransomware injection. In last 5 days we got a lot of complains about links to ransomware downloading, hidden with advetiserment of downloading “the last and the safest version of your browser”. Of course, such ad can be seen even if you are using the latest version of your browser. After opening this “browser update” file your files will be encrypted with Jope ransomware.
UPD. 15.04.2020 Synchronised with Mado, Jope ransomware developers started e-mail spamming, too. The main target of this spamming are U.S. customers of DHL, FedEx and Amazon. Common method is sending a message about unpaid invoice, with attachment of this false invoice, that contains ransomware. Of course, no real invoice is attached, but a lot of users just cannot remember, how much have they ordeged and can only guess what delivery they need to pay now.
UPD. 16.04.2020. For the last week (started 13.04) a lot of cases of Jope ransomware was likely a joint action with SAntivirus. That is a potentially unwanted program – PUP, which can cause not serious but annoying issues during your PC performance. So if you get SAntivirus – that could be a reason to check your computer with an anti-malware software.
SAntivirus can also be a very mean. According to the several reports we got from users who got Jope ransomware in pack with SAntivirus, this PUP can block your anti-malware software with a referense to it’s vulnerability to malware injection. Meanwhile, your antivirus program could detect ransomware injection much earlier then it starts it’s action.
UPD. 18.04.2020. We got a lot of report about Jope ransomware distribution through Gnutella torrent-tracker. Peering networks are hard-to-track, so you never know who is sharing a file to you. That’s why it’s quite easy to distribute any malware, including ransomware, via torrent-trackers.
UPD 20.04.2020 The next torrent-tracker is under attack. Now we are talking about 1337x, the torrent-tracker, which users reported about a lot of Jope ransomware cases. Ransomware was been distributed through seedings. There is no strict statistic about which seedings are the most “popular” for Jope distribution, because that’s a lot of different malware that is distributed in such way.
UPD 27.04.2020. Seems like a lot of last Jope ransomware attacks were caused by distributing it via another one e-mail spamming. Now, the users are complaining about tons of e-mails from unknown mailboxes. Such e-mails are offering to install an add-on for your browser, “which can track a current statistics of coronavirus disease”. As soon as you download this “add-on” and try to install – Jope will start encryption instantly.
The newest “trend” of e-mail spammers is ransomware inside the message, which contain an information aboun jobless payments. Of course, such information is completely false, but to check this out you need to download an attached .docx or .pdf file. This file contains nothing important, but has a Jope ransomware inside. The virus starts encryption instantly after the fake file was been opened.
To sum up, what can you do to avoid the injection of the Jope ransomware into your device? Even though there is no 100% guarantee to prevent your PC from getting damaged, there are specific tips I want to give you to avoid the Jope penetration. You must be cautious while installing free software today.
Make sure you always read what the installers offer in addition to the main free program. Stay away from opening suspicious e-mail attachments. Do not open files from the unknown addressees. Of course, your current security program must always be updated.
The malware does not speak openly about itself. It will not be mentioned in the list of your available programs. However, it will be masked under some malicious process running regularly in the background, starting from the moment when you launch your computer.
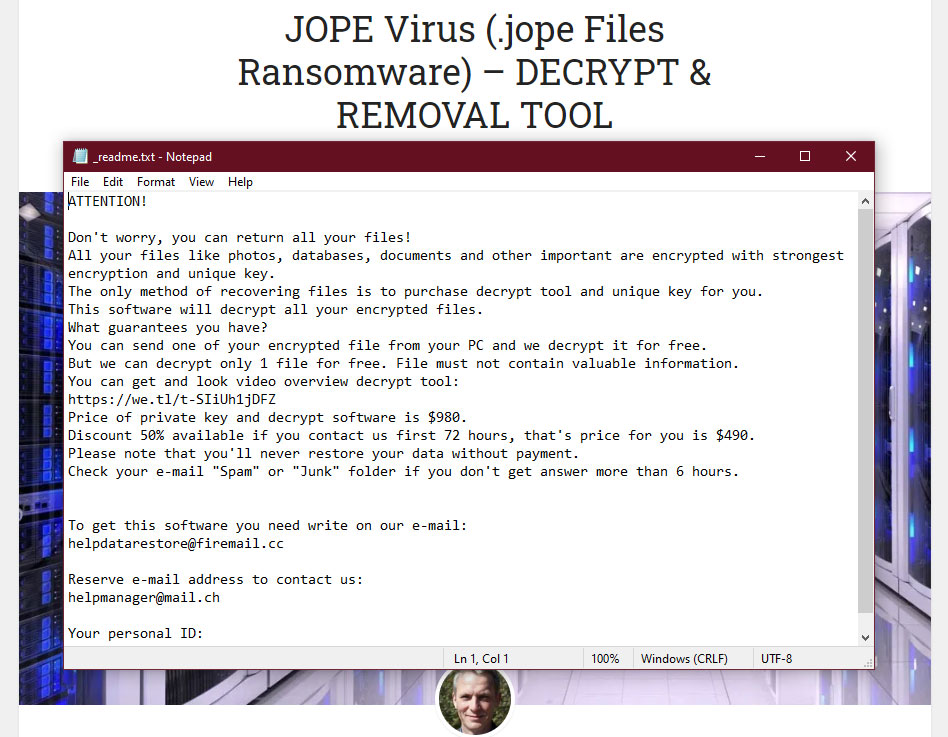
The message by the Jope ransomware states the following frustrating information:
ATTENTION! Don't worry, you can return all your files! All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key. The only method of recovering files is to purchase decrypt tool and unique key for you. This software will decrypt all your encrypted files. What guarantees you have? You can send one of your encrypted file from your PC and we decrypt it for free. But we can decrypt only 1 file for free. File must not contain valuable information. You can get and look video overview decrypt tool: https://we.tl/t-SIiUh1jDFZ Price of private key and decrypt software is $980. Discount 50% available if you contact us first 72 hours, that's price for you is $490. Please note that you'll never restore your data without payment. Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours. To get this software you need write on our e-mail: helpdatarestore@firemail.cc Reserve e-mail address to contact us: helpmanager@mail.ch Your personal ID: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
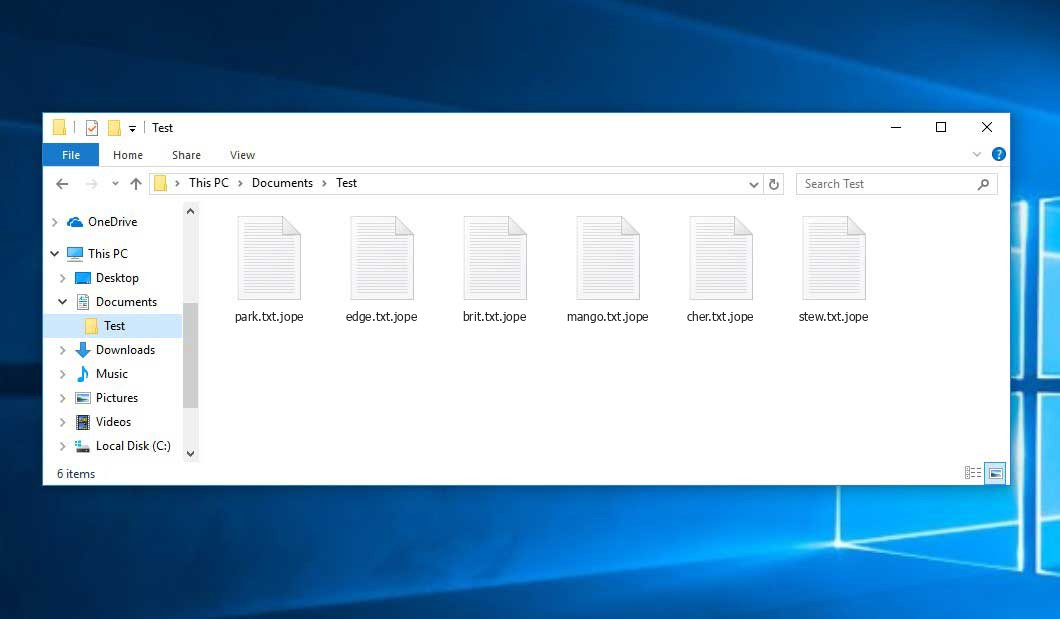
The image below gives a clear vision of how the files with “.jope” extension look like:
Two days ago, I downloaded a program from the Internet and suddenly all of my files had an extension called “.jope” added to its original extension.
I immediately had to install my PC’s operating system again.
In addition to the files saved on a separate HDD, they all have the extension “.jope” and I can’t open the files. How to restore a file that is attacked by a virus – Jope Ransomware?From letter
Bad bad bad news for me!
A ransomware (jope) attacked my personal laptop and has encrypted all my files in the laptop. Im not able to open/play any file or video.
And I used anti-virus to remove the ransomware. But the files are still encrypted! No idea how to recover!
Dont download or open any false website by mistake. Also you could be safe by:
- Take backup of all important and req files into a external hard-disk
- In windows, Create Restore point
This will help you to restore the system back to the time before ransomware happened.
N.B. Creating backups with proprietary Windows program still cannot gurantee that you will be able to use that backup for your system restoration. Some versions of the Jope ransomware can block an access to backup files, created with Windows tools. That’s why for your own confidence it’s better to have another backup mechanism that will create a separate file, and highly-desirable for you to hold this backup on an external HDD, for example.
“Sir i was able to save my 50% data and I installed new windows. Is my data secure now or there is any chance of encryption of my data please guide what should i do”
Yes,you can reinstall Windows to deal with ransomware. But you need to be sure that no files from D:/ was been encrypted or contaminated, because reinstallation of Windows can only clean C:/, if you wouldn't choose to clean D:/ in process of reinstallation. Another risk you can meet is that some important files that was been on C:/ and probably was been encrypted will be deleted because of mentioned reasons.
How to remove Jope virus?
In addition to encode a victim's files, the Jope virus has also started to install the Azorult Spyware on PC to steal account credentials, cryptocurrency wallets, desktop files, and more.
Reasons why I would recommend GridinSoft5
The is an excellent way to deal with recognizing and removing threats - using Gridinsoft Anti-Malware. This program will scan your PC, find and neutralize all suspicious processes6.
Download Removal Tool.
You can download GridinSoft Anti-Malware by clicking the button below:
Run the setup file.
When setup file has finished downloading, double-click on the setup-antimalware-fix.exe file to install GridinSoft Anti-Malware on your PC.
An User Account Control asking you about to allow GridinSoft Anti-Malware to make changes to your device. So, you should click “Yes” to continue with the installation.
Press “Install” button.
Once installed, Anti-Malware will automatically run.

Wait for the Anti-Malware scan to complete.
GridinSoft Anti-Malware will automatically start scanning your PC for Jope infections and other malicious programs. This process can take 15-20 minutes, so I suggest you periodically check on the status of the scan process.
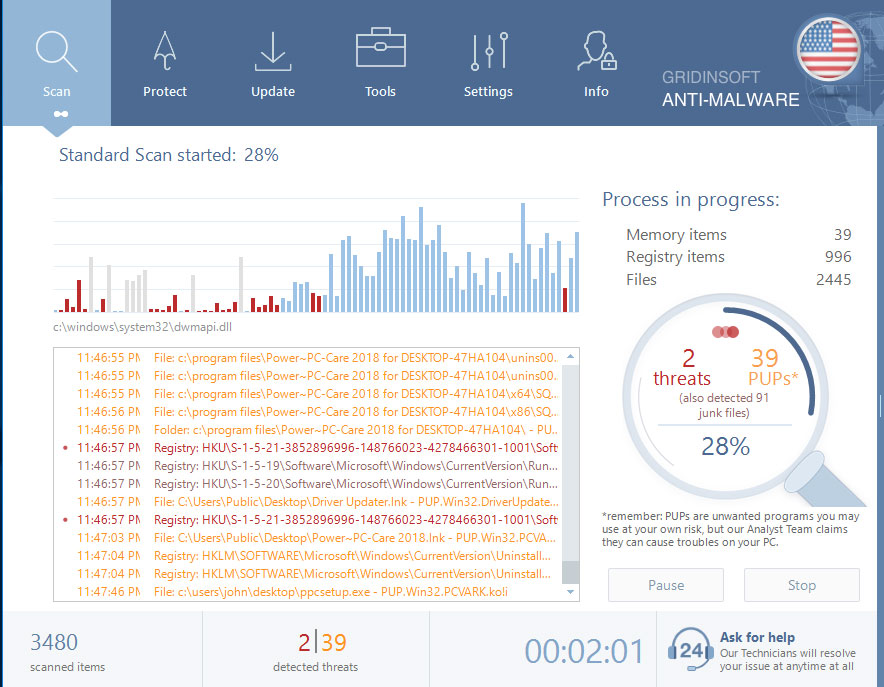
Click on "Clean Now".
When the scan has finished, you will see the list of infections that GridinSoft Anti-Malware has detected. To remove them click on the “Clean Now” button in the right corner.
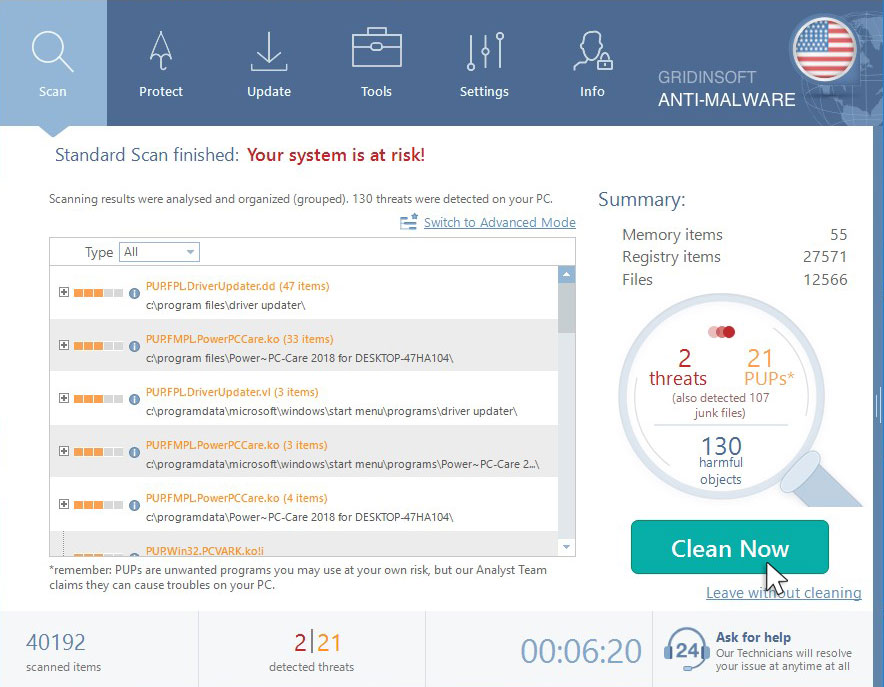
How to decrypt .jope files?
Restore solution for big “.jope files“
Once again : try removing .jope extension on a few BIG files and opening them. Either the Jope infection read and did not encrypt the file, or it bugged and did not add the filemarker. If your files are very large (2GB+), the latter is most likely. Please, let me know in comments if that will work for you.
Sai Krish, from Twitter
The newest extensions released around the end of August 2019 after the criminals made changes. This includes Mado, Opqz, Npsk, etc.
As a result of the changes made by the criminals, STOPDecrypter is no longer supported. Tt has been removed and replaced with the Emsisoft Decryptor for STOP Djvu Ransomware developed by Emsisoft and Michael Gillespie.
You can download free decryption tool here: Decryptor for STOP Djvu.
Download and run decryption tool.
Start downloading the decryption tool.
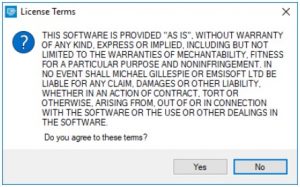
Make sure to launch the decryption utility as an administrator. You need to agree with the license terms that will come up. For this purpose, click on the "Yes" button:
As soon as you accept the license terms, the main decryptor user interface comes up:
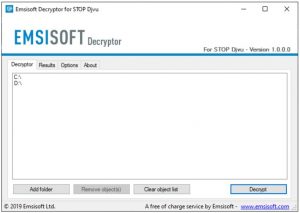
Select folders for decryption.
Based on the default settings, the decryptor will automatically populate the available locations to decrypt the currently available drives (the connected ones), including the network drives. Extra (optional) locations can be selected with the help of the "Add" button.
Decryptors normally suggest several options considering the specific malware family. The current possible options are presented in the Options tab and can be activated or deactivated there. You may locate a detailed list of the currently active Options below.
Click on the “Decrypt” button.
As soon as yo add all the desired locations for decryption into the list, click on the "Decrypt" button in order to initiate the decryption procedure.
Note that the main screen may turn you to a status view, letting you know of the active process and the decryption statistics of your data:
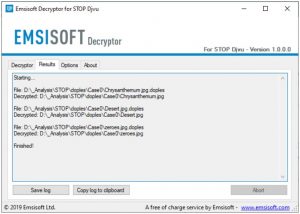
The decryptor will notify you as soon as the decryption procedure is completed. If you need the report for your personal papers, you can save it by choosing the "Save log" button. Note that it is also possible to copy it directly to your clipboard and to paste it into emails or forum messages if you need to do so.
Frequently Asked Questions
How can I open ".jope" files?
jope files contain important information. How can I decrypt them urgently?
If not, then you can try to restore them through the system function – Restore Point.
All other methods will require patience.
You have advised using GridinSoft Anti-Malware to remove Jope. Does this mean that the program will delete my encrypted files?
You need GridinSoft Anti-Malware to remove active system infections. The virus that encrypted your files is most likely still active and periodically
runs a test for the ability to encrypt even more files. Also, these viruses install keyloggers and backdoors for further malicious actions
(for example, theft of passwords, credit cards) often.
Decrytor did not decrypt all my files, or not all of them were decrypted. What should I do?
We will keep you posted on when new Jope keys or new decryption programs appear.
Why is the JOPE decrypter stuck on "Starting"?
What can I do right now?
- In the United States: On Guard Online;
- In Canada: Canadian Anti-Fraud Centre;
- In the United Kingdom: Action Fraud;
- In Australia: SCAMwatch;
- In New Zealand: Consumer Affairs Scams;
- In France: Agence nationale de la sécurité des systèmes d’information;
- In Germany: Bundesamt für Sicherheit in der Informationstechnik;
- In Ireland: An Garda Síochána;
Video Guide
It's my favorite video tutorial: How to use GridinSoft Anti-Malware and Emsisoft Decryptor for fix ransomware infections.
If the guide doesn’t help you to remove Jope virus, please download the GridinSoft Anti-Malware that I recommended. Also, you can always ask me in the comments to get help. Good luck!
I need your help to share this article.
It is your turn to help other people. I have written this guide to help people like you. You can use the buttons below to share this on your favorite social media Facebook, Twitter, or Reddit.
Brendan SmithUser Review
( votes)References
- Ransomware-type infection: https://en.wikipedia.org/wiki/Ransomware
- Twitter: https://twitter.com/demonslay335
- My files are encrypted by ransomware, what should I do now?
- About DJVU (STOP) Ransomware.
- GridinSoft Anti-Malware Review from HowToFix site: https://howtofix.guide/gridinsoft-anti-malware/
- More information about GridinSoft products: https://gridinsoft.com/comparison



Do you have offline or online key?
i have online key. How to fix this ? ASP
thanks
Check the C: drive for the SystemID/PersonalID.txt file – it contains all of the ID’s involved in the encryption.
YS9IveiZGjji6SY6TyRqK40qD34Jqw21OLQJuLB0
IS it online OR offline ID?
This is online ID
hLtvi94ohUTNIQ1VkAcAgNoGgU8uSWNdMq8Gwcky
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-SIiUh1jDFZ
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
helpdatarestore@firemail.cc
Reserve e-mail address to contact us:
helpmanager@mail.ch
Your personal ID:
0218OIWojlj48CFv6kXoepFYesnjrqMPVqdlnJOannRUsVccBCeL0
yawa ka
Help me recover my data. Yesterday the (.jope) virus infected 70% of my data. I have two discs for PC, the virus has infected only one, on the other disk all data can be read. Why?
Please help me recover my files infected virus .jope
” No key for New Variant online ID: FF3psWU89MUxuzSRntTknhw2Tl3P0NZdEuSDWgBB ”
” Notice: this ID appears to be an online ID, decryption is impossible ”
in the readme.txt virus attention
personal ID:
0218OIWojlj48FF3psWU89MUxuzSRntTknhw2Tl3P0NZdEuSDWgBB
Your personal ID indicates that you have files encrypted by an online key and they won’t be decryptable.
Sorry. Try other methods.
0218OIWojlj485pAW5jtxzZu4RwpTDsDHndcFCchnQzwCYOM0KSeU
online key
Please help me recover my files if any have a clue!
Ransomware with name extension (jope)
i have online key…
thanks
They are not decryptable by Emsisoft. Try other methods.
.jope Attak my pz plz help me
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-SIiUh1jDFZ
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
helpdatarestore@firemail.cc
Reserve e-mail address to contact us:
helpmanager@mail.ch
Your personal ID:
0218OIWojlj48CFv6kXoepFYesnjrqMPVqdlnJOannRUsVccBCeL0
Ransomware with name extension (.mado)
Hi sir I am infected with jope virus. this is my ID. This can be ecrypted?
4cjuZPKHcIPN2SeQpYF6uTaVnPsHS5Z7Sw4Ezv68
Thanks with regards
please suggest another method
Sir i was able to save my 50% data and I installed new windows. Is my data secure now or there is any chance of encryption of my data please guide what should i do
hello
this is my ID 0218OIWojlj48R3LChyUAg0YHXiGP7S8i2Lj12J9fPGkhHlu40I1f
how can i know if im offine or online version?
what can i do?
i dont have any valid point of restaure…
Sorry, this is online key
kISaVbGTMb38x9B2Ei9PVeWmKI6hZjnRLd1p1Wy2
Thats is offline??
Please reply
Sorry, this is online key. Use Restore Point: https://howtofix.guide/system-restore-point-windows-10/
0218OIWojlj48EePN3LHgmRwL1zq2RrbHB488hr7iirVpzVkWtnCk is this online or offline?
Infected with with .jope
ID :
K72FcnkdIQC15Y6gSOcshlkpUbvUZNl4zrQFK1t1
G6viTtTUUUgc7WwuXDMjUOMtAHQQlcWkevsSicL9
Online or Offline ?
I’ve found a suspicious key inside an encrypted file, i opened it as notes and i found that :
“My personal ID”{36A698B9-D67C-4E07-BE82-0EC5B14B4DF5} and this note is closed and when i open it it display as algorithm that u can’t understand it .
What is that?
Thanks in advance.
Your personal ID:
0218OIWojlj48K72FcnkdIQC15Y6gSOcshlkpUbvUZNl4zrQFK1t1
ID:
0218OIWojlj48K72FcnkdIQC15Y6gSOcshlkpUbvUZNl4zrQFK1t1
Please help me recover my files infected virus .jope
ID:IloKH49aDkZ2zKqSFumUeBCyTZqgDnxBZyMaUZlb
Hi: I cant fix my data file plez i need your help .any file have jope name .
my ID of line . t1
0218OIWojlj48K72FcnkdIQC15Y6gSOcshlkpUbvUZNl4zrQFK1t1
My computer is infected .ADHUBLLKA ransomeware
in notepad says
—= GANDCRAB V5.1 =—
***********************UNDER NO CIRCUMSTANCES DO NOT DELETE THIS FILE, UNTIL ALL YOUR DATA IS RECOVERED***********************
*****FAILING TO DO SO, WILL RESULT IN YOUR SYSTEM CORRUPTION, IF THERE ARE DECRYPTION ERRORS*****
Attention!
All your files, documents, photos, databases and other important files are encrypted and have the extension: .ADHUBLLKA
The only method of recovering files is to purchase an unique private key. Only we can give you this key and only we can recover your files.
The server with your key is in a closed network TOR. You can get there by the following ways:
—————————————————————————————-
0. Download Tor browser – https://www.torproject.org/
1. Install Tor browser
2. Open Tor Browser
3. Open link in TOR browser: http://alcx6zctcmhmn3kx.onion/?d756e65476c65746e49656e695bfc3cbb7fd12
4. Follow the instructions on this page
—————————————————————————————-
On our page you will see instructions on payment and get the opportunity to decrypt 1 file for free.
ATTENTION!
IN ORDER TO PREVENT DATA DAMAGE:
* DO NOT MODIFY ENCRYPTED FILES
* DO NOT CHANGE DATA BELOW
—BEGIN GANDCRAB KEY—
s01drtwRz02BYl9TeuLkD4uNv7gzlwCqaBds5b0p9IER1dPtuKjaO/WuQ2AMxuS9K7HASJNoaZi/D/oldpEDoELvhsmS0nQO5o26UpJGYjR3EOUi1qzvGt6Ct3jSgLQMfT1YK8BbLXbKULBJeIlSmYiavVewUOAE+fEeDdYw2q1FlElqBG52WLpIWncN2NKUFe98J+ej4aYlzWGss8uPvJzk6fCDPO6auPu8alAAlbyleLEuRPgNdaQBfprj8L4Y9wnJ8pyv5/RlPcfysnMA0v//2pk073m+KcMGmaIh1AIOGJQ/ojYXd79XATBpoNAdBzOMv8dPUMFUuCu52DmUzqUZNmxHvKxUVh0BZ+w+zWol0qjL6fkbgEcKhUycV/Mo/0nSYZ90q70nH1cGVpqWH/EMAE2D2xn2vlBv3JijwRbvCLckesIBUe4n/Gww6Hhsh1PdiDYbtsTFhVxVw2emwGd03u5BoXfL6pqBujXWoRku8nfE2ppbl5LkCfqwRlWOTRkRaUTkXb8Gp9Rfa0lwj8buVWNOnHInlCPNHeGEIV19CpkdRiZ0Btb/vPCsmMUlbhwvqoAYPVnwe1BIp15drpKlIosFToSWiLREWvgJcTsDzmUTkGMM9mh8dlCVjHzNDe4XBs9vYpWX+TZXFC0qUejnYnQo14s6jg0d7nbo+LyGRCK2E94NIdVxuGJbDNclfzolLu5hb+VuwEEoU22RtDRYRvUtxIE4TeFfR0H00iwZEdJiYbOx2s5NqcHcyrqCmOmmJ4/S9GOLYyv664Hll250GP6UjjfFZh47dEOrPCD7fKH4k9Amx1Rtndg9oudqF1WmtF8YN0las/FNXD6fX9tWCPMl13l0qea9Q3b/VqVvcfVgyY7H4JP+xDjOCOmxj13Wthebei0DzJ4VIb9xeBTXyfFSAXWcbK4IrPdFdn10EPEdCGbG4bhdliDZRtjhc9/No4K0Bh56/1BDnnPsV81KNy+ZT/Y0VBdv24hC+2iwebPe7UZfXMnoyID8jLqYTgXUaa7IQVkX1Wc3/Bgc9tXfyVrFO2G/th1+RlhwrMkWl9ZNpGC9YDVrxz8gqWTR0vCmBAy6TQzS1uuKjwEZoTdGOT/FeyXokXvIDu7juv+veLrcawXUjYcgpjpH+YN6+Z8KU+VaEXbzRwLkcWAUpWV24UokEwuCv3cyH+sAa7BSBzsJwS26f5O8aipmx2PS0N9O8t9jUQ9pr49uUPngA6PjgdIX6CTJPTUQ/mYNBVvgTV8BT+NKKp0rhFekuPtgkI+y1vbG8rsReuvcbIxE14ydmVwY1yiW9RU3lOCKcg3Ny8P+1ApoeBbQHRzoabLJo4Ll0DdEeHmnAp8NhZTzkUQQz2ZBw==
—END GANDCRAB KEY—
—BEGIN PC DATA—
wfKD6iudumBkmpL8IRr4U7OxBlagOWntnTwmOrT1y1YWvOiWMx5GYaRdvZZETpJRrHYJ7n1WsLfHTGOH5B5eBM3zytMV76z6YkGADDviApJk883FeP/4mGGoAZACLp+j5fx02W/xA5LHiq+hWUTkAr4AjbZbOKiX5bnMbVUkLHQnbYuWlMCiYZhYRKSGxpopEI4/25+AYlKFZF1V8QPIuXHcMCJz2OuMKEPmMPYPkYpSLE2TNJxRmtUoSnZiP6U/BPr01s5zijbhjcBAA3g8l9FnZN0zCBMxYg7XDNIroX07SivFDg+ukastGdjvqY+nk7rs57xivbEmkRnBouLw/3A2TutlGrRYPlraBmPtoBGeEd8bpScE4pu4aqa/Y4hyNoz+2RSimJRPTWIqP1PqJIcJoJFgwNUoBRPOnKg+We4MALefhWEyg6hrLw3/xFZKlA6jZiLpehFH3oPLSObB13MZRXR5RlCKfjnV1lPgfH8LmUHfnCz1QUpnn7ImltCw6XIOVYzpfzfyfBMce8BiP3VNgH9eQ23Cr6ZIEpXtVUjABfxMGZGaHp4Oe7/LRdoPool/V6fu5bPBzMH9PHYBh9Ez6uxNRfttWv/ebjnWueITXpBeJdRy9BZhN1Lc2rlgkmnMLRQz3AtWfgj5R2EKiTIEy7IFT7fbAgE0KYz/jzModCw37W5bfaaU5HJ6LfC8RB0KXb0DFtZxjWPfxwrBwnounsV5mNrglYqoOg==
—END PC DATA—
thanks
0218OIWojlj4849MGkdA2R5lsGfdlpqcpflP7akiLKLbO4RmVTcmV
DEAR SIR
THIS IS MY ONLINE JOPE ID, MY ALL DATA GOT ENCRYPTED BY JOPE RENSOMWARE, NOT ANY FILE CAN BE OPEN. PLZ HELP ME OUT TO RECOVER ALL THESE
Xin chào người anh em, làm ơn giúp tôi kiểm tra ID của tôi là khóa trực tuyến hay ngoại tuyến?
ID: K72FcnkdIQC15Y6gSOcshlkpUbvUZNl4zrQFK1t1
cảm ơn